If you want to transfer files to your web server or manage its database remotely via the WordPress Command Line Interface (WP-CLI), you’ll need your SSH (Secure Shell) credentials.
Let’s cover what you need to know about SSH and where you can find the SSH credentials in the dashboard in the Nexcess Client Portal.
What is SSH (Secure Shell)?
SSH (Secure Shell) is a secure network protocol used for encrypting communications over unsecured networks. Typically, you use it to log in to your server from a remote computer such as your home desktop or laptop.
SSH provides encryption on both ends — the server and the client — to keep the entire session secure. It’s an improvement over file protocols such as RSH, which uses plain text communication during data transfer.
Advantages of SSH (Secure Shell)
SSH (Secure Shell) comes with several benefits over other protocols:
- Open Source: OpenSSH, the most popular implementation of SSH, was developed in 1999 under an open source license. As a result, you can find many free SSH-supported clients.
- Tested Security: Given its open-source nature and long presence in the market, it’s a battle-tested protocol that you can always trust.
- Popularity: Due to its strong security, it comes installed by default on almost every Unix-based operating system. In other words, it’s a ubiquitous protocol you’ll always find support for.
Popular use cases for SSH (Secure Shell)
Given its robust security, you can use SSH (Secure Shell) to:
- Log in to a remote server.
- Execute command on a remote server.
- Have passwordless logins to a server.
- Transfer files efficiently and securely.
- Mount a directory from a remote server while making it part of your file system via SSH Filesystem (SSHFS).
- Monitor and manage servers.
What is SFTP or SSH File Transfer Protocol (FTP)?
SFTP, or SSH File Transfer Protocol (FTP), is an implementation of SSH used for accessing, transferring, and managing files over a network.
While SFTP and FTP sound similar, their similarities don’t go beyond the name and function. Unlike FTP, SFTP is made from the ground up using SSH (Secure Shell) protocol, which makes SFTP more secure than FTP.
For other security-related queries, explore the Security category within the Nexcess Knowledge Base.
Secure Shell (SSH) user setup differences between hosting plans at Nexcess
At Nexcess, the Secure Shell (SSH) user setup depends on your web hosting product and platform:
- On Managed WordPress (MWP)/Managed WooCommerce (MWCH) hosting plans, each website has its own individual SSH user.
- On all other Nexcess Cloud plans (Magento, Flex, etc.), each hosting plan has its own SSH user.
- There are specific nuances with regard to team member credentials related to the Secure Shell (SSH) user setup for web hosting teams.
How to access your Secure Shell (SSH) credentials
Now that we’ve covered the basics of SSH let’s see where you can find your SSH credentials in the Nexcess Client Portal.
1. Log in to your Nexcess Client Portal:
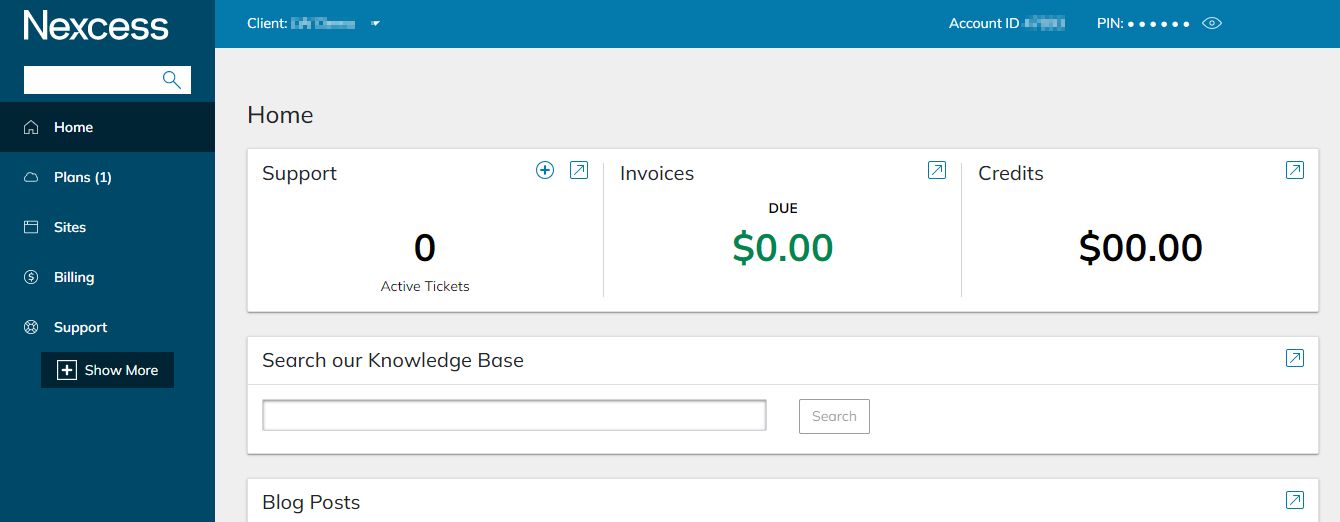
2. Go to the Plans area in the user interface:
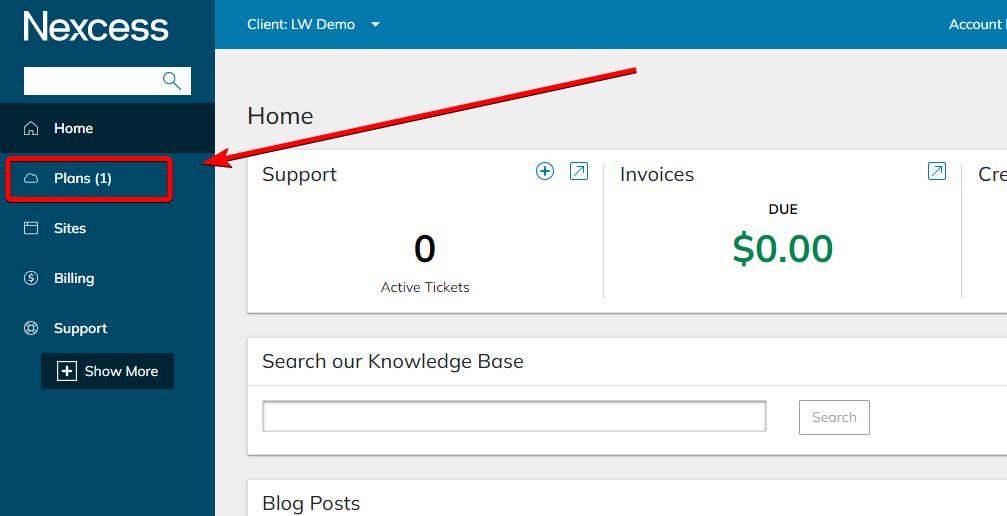
You can see all your active plans in this place. In this example, we'll be working with the WordPress plan:
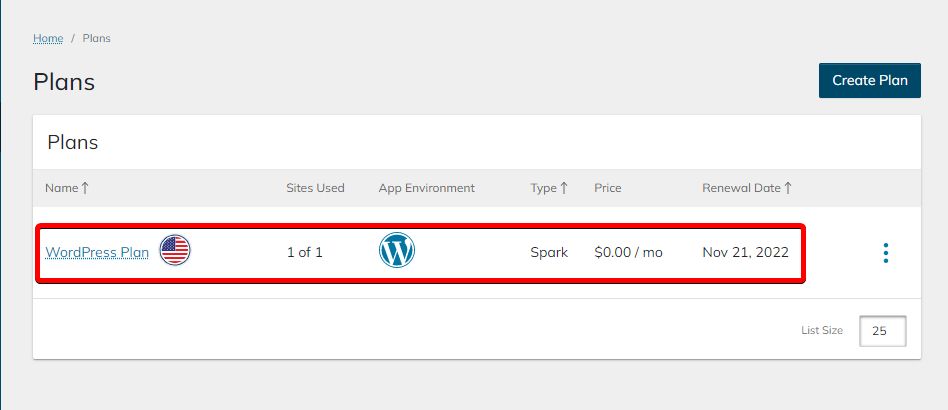
3. Now we need to reach our Plan Dashboard. To do so, click on the vertical ellipsis that can be found on our right-hand side to see your WordPress plan options:
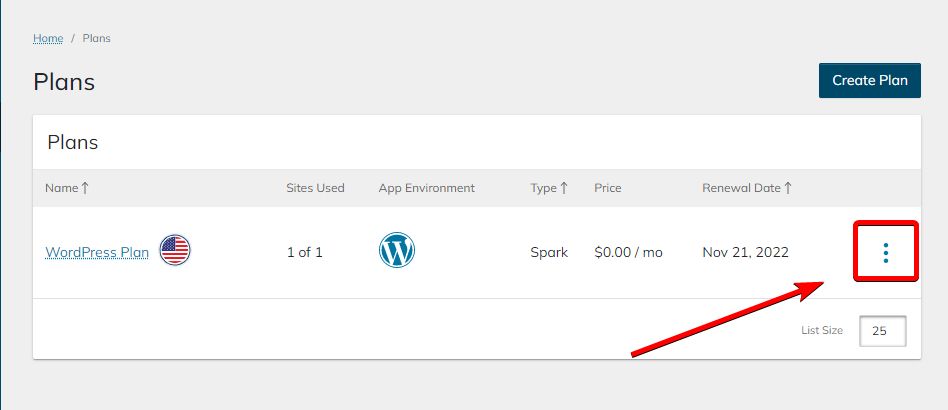
4. Navigate to the Plan Dashboard:
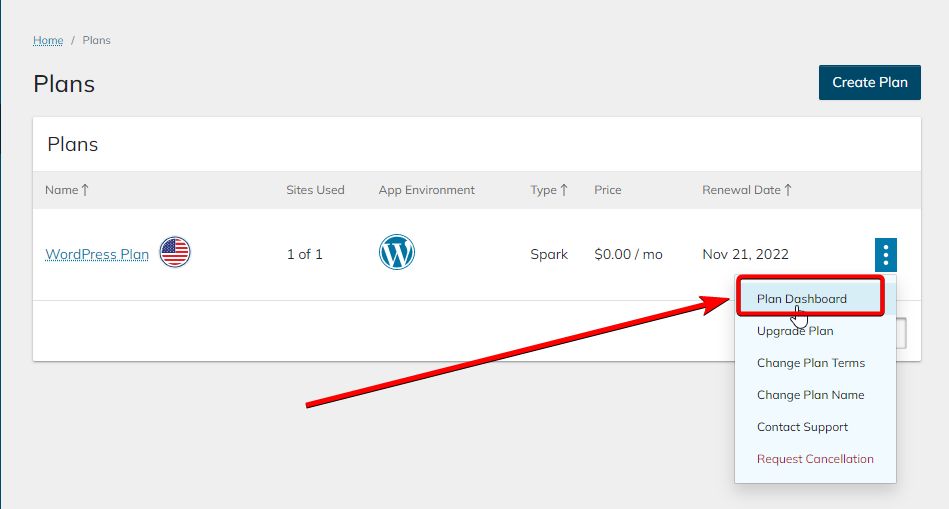
You’ll see a list of websites you have on the plan. First, find the website you want to create SSH (Secure Shell) credentials for:
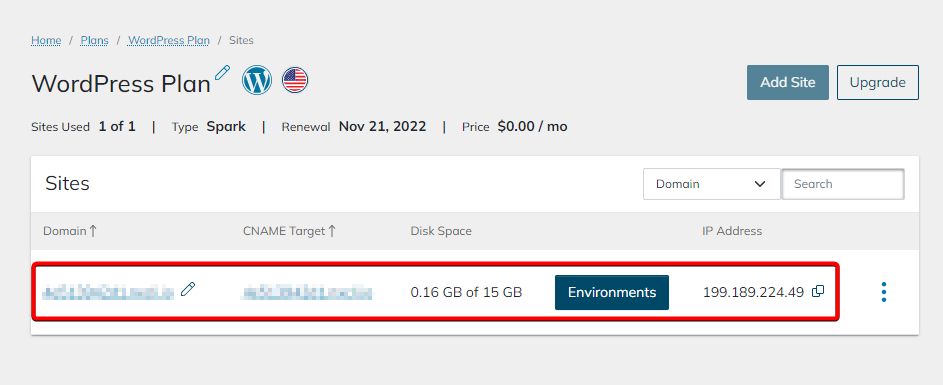
5. Open site options by clicking the vertical ellipsis and navigating to Site Dashboard:
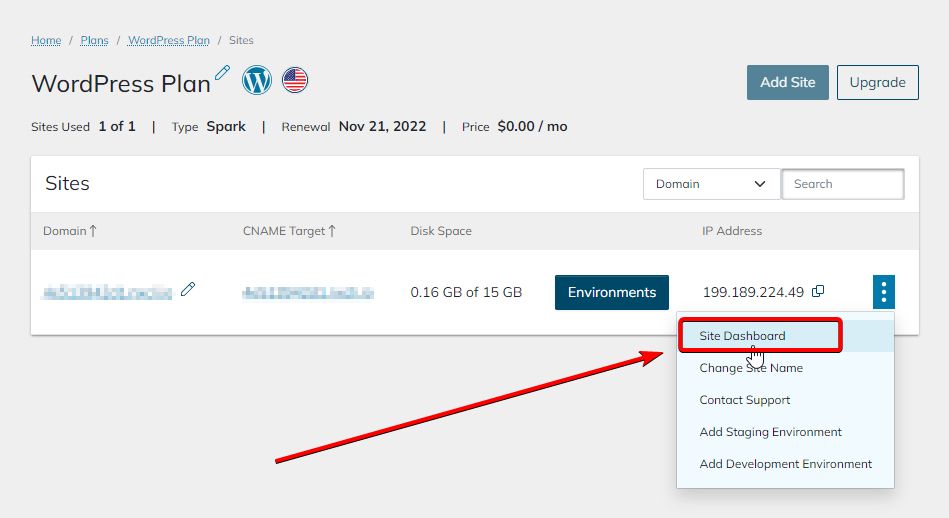
In the Site Dashboard, you’ll find Secure Shell (SSH/SFTP) credentials near the top of the page. You can also change the password by clicking the Generate New Password button location in the bottom right portion of the Secure Shell (SSH/SFTP) box:
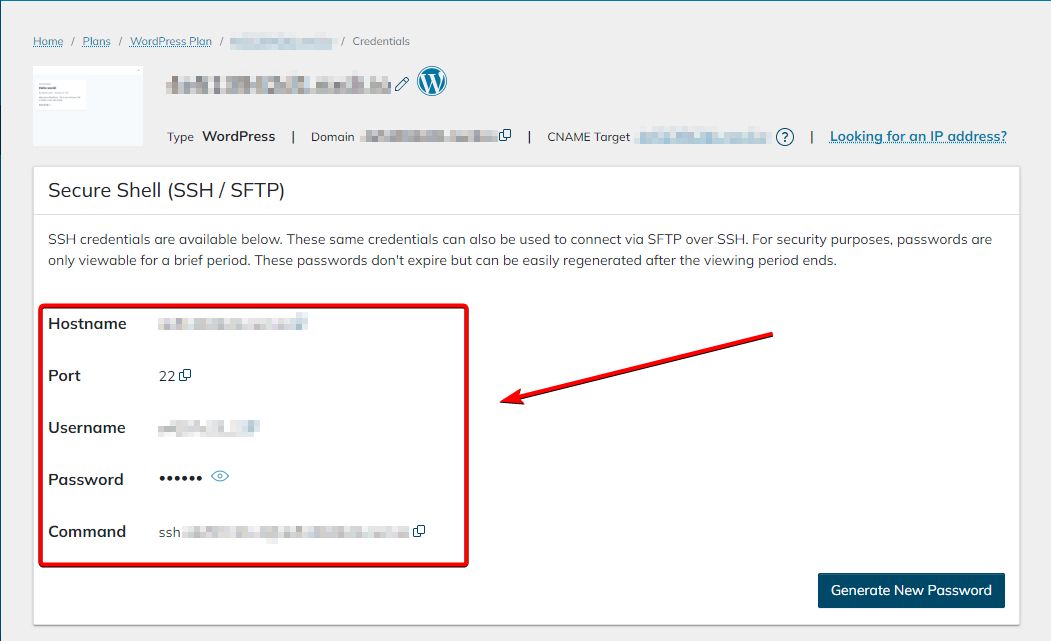
Check out the SSH category and other categories within the Nexcess Knowlesdge Base to study the many features of the Plan Dashboard and Site Dashboard in the Nexcess Client Portal.
What are SSH (Secure Shell) keys?
Instead of using passwords to log in to your remote servers, you can also use SSH keys. SSH keys refer to a pair of keys consisting of one public and one private key.
When you attempt to log in to the server, the server sends an encrypted challenge request via the public key. You can use the private key to decrypt the request and send a response to the server, which in turn will give you access to the server.
SSH keys are more secure than passwords as their complexity makes them more resistant to brute-force attempts. Also, you don’t send a password to the server, so you don’t have to worry about data transfer risks.
While they offer higher security, they aren’t without risks and unique challenges. For example, if your laptop with the private key gets stolen, someone could gain access to your server.
Not to mention, if you’ve too many SSH keys in an organization, it can be challenging to track them and manage server access.
Check out how to add SSH keys to your Nexcess Cloud account to learn how to add SSH keys to your cloud hosting plan.
Final thoughts — guide to using SSH (Secure Shell) credentials with your Nexcess hosting plans and sites
Now that you know how to find the SSH credentials, you can use them to control your web server and upload files remotely. In addition, SSH ensures that the link between you and the remote server remains secure, and you can do your work without worrying about data risks.
What kind of WordPress support do you offer?
Nexcess provides 24/7/365 expert WordPress support for every customer by phone, email, and chat.
If you want a web hosting partner to rely on for your security needs, consider Nexcess managed hosting plans for WooCommerce.
Note about the original publication date
This article was originally published in October 2019. It has since been updated for accuracy and comprehensiveness.