Behind every dynamic website and interactive application is a database that stores critical information. Every organization that owns an application — native or web — understands that databases are key to their success.
That explains why you’re reading this guide. You want to learn about database security best practices so you can implement them for your enterprise.
We’ll briefly discuss the consequences a database security breach could have on your organization. Then, we’ll review security practices your company should adopt to proactively protect your data from bad actors.
But first, understand the common threats you’re up against. That way, you can carefully develop strategies to strengthen your organization’s data security.
Here’s what’s in store:
- Common database security threats
- Enterprise database security best practices
- Final thoughts: 9 enterprise database security best practices
Common database security threats
There are numerous security threats your organization will likely face over the years. Here are some common ones:
- Malware: This is malicious software built to steal or corrupt data.
- Human errors: Your staff will make costly mistakes every so often — it’s inescapable.
- SQL injection attacks: SQL attacks aim to exploit poor input validation. They manipulate database queries to retrieve restricted data. In some cases, they lead to significant data loss or corruption.
- Insider threats: Sometimes, a bad actor will come from within your organization. Even one self-serving employee can compromise your database.
As simple as the threats sound, they can quickly cripple an organization.
Most database management systems have built-in security mechanisms to ward off common threats like these. So why do you need to deploy additional security measures to protect your database?
The importance of database security for enterprises
Imagine your enterprise has a website that stores ecommerce data from customers across the country. This data includes names, phone numbers, emails, and home addresses. All of this helps your company serve its customers more efficiently.
But if a hacker gains access to that data, they can call customers while pretending to be representatives of your company, and dupe people into sending money. Not only will customers leave en masse, your reputation will be tarnished and you may even get sued.
The average cost of a database security breach is huge. In the U.S., it stands at $9.44 million. This often manifests as revenue loss, lawsuits, and policy violation fines from the government.
This is precisely why database security is important. But you wouldn’t be reading this guide if you didn’t know about the potential disasters of a data breach.
So let’s explore how data security best practices prevent things from going wrong, potentially saving your company millions in lost revenue.
Enterprise database security best practices
1. Limit access levels as much as possible.
2. Encrypt sensitive data.
3. Secure the physical location of your database.
4. Keep database servers separate from application servers.
5. Back up databases regularly.
6. Monitor databases frequently.
7. Deploy application and database firewalls.
8. Prevent public network access.
9. Don’t use default network ports.
So far, we have mentioned database security best practices a few times and reiterated their importance in safeguarding your customers’ data. It’s time to go over each of these best practices.
In the following sections, you will learn specific actions you can take (with the help of your colleagues) to secure your databases further.
Most of the steps below require a working knowledge of your company's database system. Even if you don’t have the skills, get a skilled colleague to help you implement these strategies. It’ll prove worth it.
1. Limit access levels as much as possible
A database management system provides users with different access levels depending on their roles and scope of work. This is important because it limits the actions each user can take without supervision.
For instance, there are database users with read rights only. They can not change the data in a table. Neither can they make changes to its schema.
As a database admin, ensure that your coworkers only have the rights they require to execute their assignments. If they need to do something outside the scope of their duties, let them ask you for permission.
Creating a protocol like this helps you closely monitor all activities on the database. It also makes it easier to identify and correct minor mistakes before they escalate to a full-blown crisis.
An equally important reason to limit access levels is to prevent the misuse of rights. Database users with excess rights can take actions that are outside their domain.
For instance, just because someone is assigned to create backups doesn’t mean they should be able to access database records and delete them without permission.
To further strengthen your protocol, start a routine audit of each of your coworkers’ rights. Consider whether they need all the rights they have, and update accordingly.
Perform these audits frequently. For instance: If, last week, a user needed writing rights to a specific table but doesn’t anymore, take away the permission.
In some extreme cases, your business competitors may plant malicious insiders in your company to wreak havoc and put you behind – which is illegal.
In some situations, it’s smart to limit access levels for everyone. This diminishes a malicious insider’s ability to cause damage.
2. Encrypt sensitive data

Every day, your website or app collects tons of sensitive data from your customers. This includes details like credit card information, residential and billing addresses, and the race or ethnic backgrounds of your customers.
We’ve already established that losing this data would be catastrophic. That doesn’t need to happen. Deploy an additional layer of security that encrypts sensitive information in your database.
Data encryption translates sensitive data into encoded data. Even if it ends up in the hands of a cybercriminal, they won’t be able to use it without an encryption key.
One thing to note is: Data encryption is more of a containment measure. It doesn’t proactively protect your database from unauthorized access. It protects your customers’ data from misuse in the event your security has been breached.
Read on to discover how to proactively secure your databases.
3. Secure the physical location of databases
Physical security is one of those often overlooked data security best practices because people forget that data is stored on objects that can be physically stolen or tampered with.
To limit physical access to your databases, try these steps:
- Ensure all vehicles are checked before parking at your building. Also, all individuals walking into the building must be fully accounted for.
- Lock your server room at all times. Only allow authorized users physical access to the database servers.
- Create strict policies for how visitors are allowed to visit your server room. For inspiration, see this facility access policy for Nexcess clients who visit its data center in Michigan.
- Put your server room, data center, and building under 24-hour CCTV surveillance.
- Install an intruder detection system, train people to use it, and create a protocol for what to do if an alarm triggers.
Out of all the database security best practices in this guide, this one is the most potentially expensive to implement. Start small, but start somewhere, and put forward a plan to gradually set up these crucial precautions.
4. Keep database servers separate from application servers
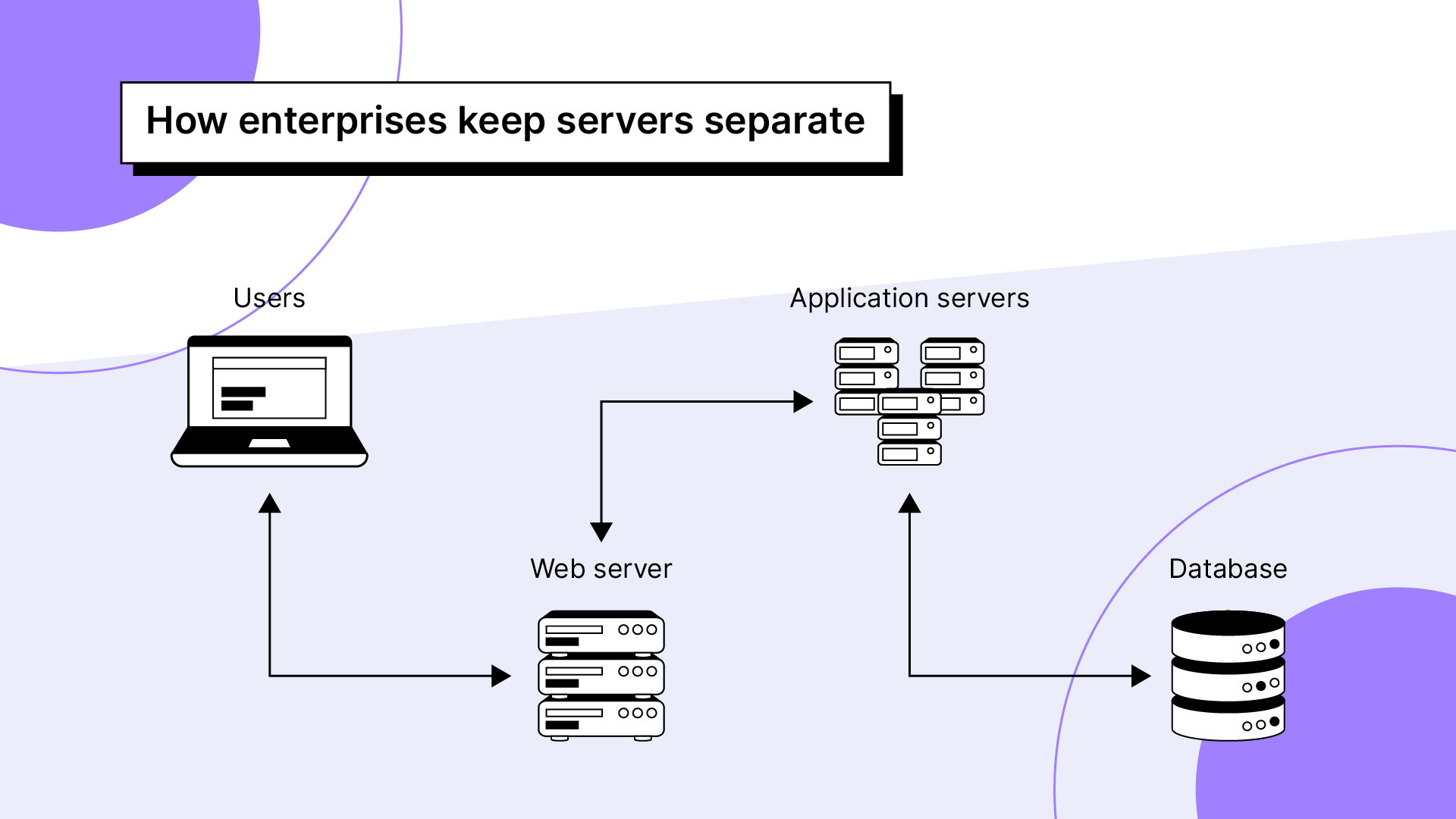
If your applications and database are hosted on the same server, that’s known as a single point of failure. When the server fails, all services will become unavailable. When the server is compromised, both the application and database will be compromised. Avoid this to improve the security of your database.
Ideally, you want to host applications and databases separately on different devices, then connect the servers over a network.
With a separate application server, if a web server makes a suspicious, incorrect, or insecure request, it won’t be forwarded to the database.
That’s because the application server acts as an intermediary communication line between the web and the database servers. Specifically, the application server receives requests from a web server and checks them for safety before forwarding them to the database.
5. Back up databases regularly
If you have worked with databases long enough, you know that data corruption happens occasionally. Corrupted data is hard to deal with after it’s happened — unless you have dealt with it preemptively. That’s the role backups play.
A good backup strategy runs on a schedule. Your schedule should be based primarily on how often your database changes. Some databases are simple: They experience little activity throughout the day. If yours is like this, create one or two backups daily.
In contrast, some databases are super busy. A high-traffic ecommerce website experiences many changes throughout the day as customers make requests. If that parallels your database, you need several daily backups.
Frequently backing up databases may seem daunting, but you don’t have to do all the backups manually. You can use cron jobs to automate the whole process.
When you’ve managed to set up frequent database backups, what do you do with the backup files? Database security best practice is to store the backup files on a separate device. That way, even if the machines hosting your database are destroyed, you’ll have a clean restore point.
However, remember that backups can also be misused. Therefore, store them in an environment that enforces strict database security policies.
6. Monitor databases frequently
Thanks to software, activities on your database can be monitored around the clock. Keep logs of all these activities in real time on a separate server.
As another layer of caution, install additional software like Data Dog on the devices where the logs are stored. The program scans the logs and tests each record against a predefined set of rules. It uses these rules to detect unusual activities and flag potential data breaches before they escalate.
As a general rule, pay special attention to accounts with high-level access. These accounts are more prone to brute-force attacks and misuse. If you monitor them consistently, you will likely discover and fix vulnerabilities promptly.
7. Deploy application and database firewalls
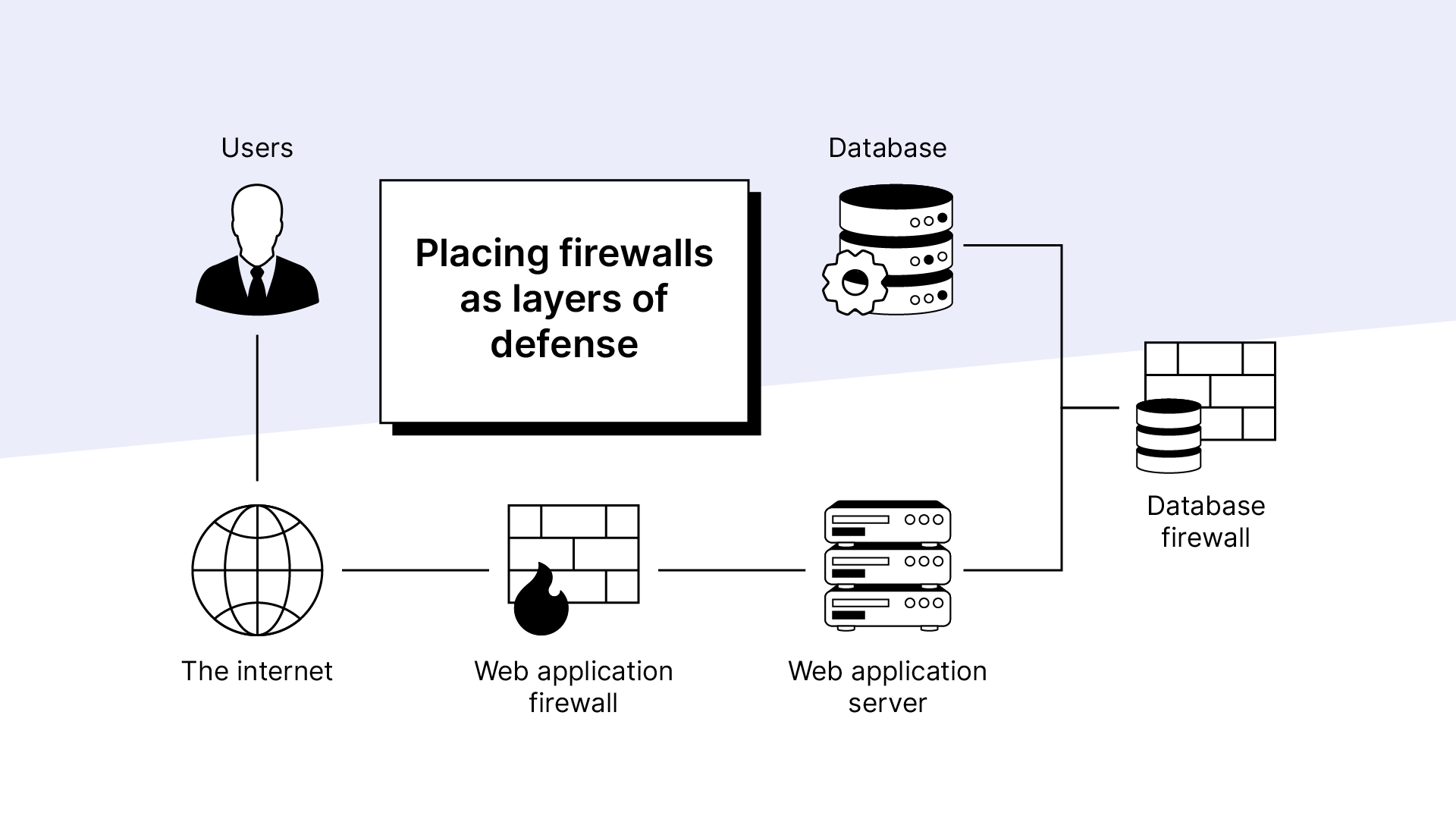
Unlike log monitoring tools, which detect breaches after they have happened, firewalls are more proactive. They filter traffic in real time before it reaches the database. Firewalls have a predefined set of rules with which they assess all traffic.
That means no single packet of data can get through to the database server unless the firewall thinks it is safe. It’s your first line of defense against an attack launched against your database.
In particular, a web application firewall (WAF) protects databases by intercepting attacks. For example, SQL injection attacks capitalize on trusted applications with permission to access the database. Since application servers may let this traffic through — but a web application firewall will block it.
Despite being excellent at detecting and blocking suspicious activities, firewalls are ineffective against some attacks, like distributed denial of service (DDoS).
To remedy this, you’ll need security solutions that precede a firewall in handling requests. Using real time IP blacklists and other advanced security solutions is useful to filter malicious traffic.
8. Prevent public network access
Your database should never be open to the public unless that is specifically why you set it up.
Your customers, being the primary users of your database, should also be allowed to access it — but only using an application built for customers to make requests.
Applications simplify the processing of retrieving and storing data, and abstract the intricacies of the process. Your customers don’t need to know how your database management system works.
Implement data security measures and access control policies that regulate how other entities, like web servers, access your database.
One of the most effective ways to restrict access to your database is hiding it behind a virtual private network (VPN). When you do this, only users you have authorized can access your database.
9. Don’t use default network ports
For two devices to communicate with each other, they need a protocol. It helps them determine how to transmit information from source to destination.
Ports and port numbers enable each device on a network to identify a specific type of transmission process. For instance: The user datagram protocol (UDP), which facilitates server communication, uses port 161 by default.
Since hackers understand how networks work, they know the default ports of the services they launch attacks against. Hackers check to see whether their target is still using default settings.
The good thing is you don’t have to use that port. You can configure your devices to use a different port to communicate. Use unique ports for all your connections. This data security best practice puts an extra barrier between you and cyber criminals.
Final thoughts: 9 enterprise database security best practices
Data protection should never come to you as an afterthought. Cybercriminals are getting smarter by the day, and cyberattacks are quieter and more lethal than ever before. Your organization’s cybersecurity should consistently be on the list of priorities you work on to prevent surprises.
Each of the database security best practices outlined here adds an active layer of security that protects your customers' data.
However, it’s okay if your organization does not have the resources to host your database on-premise. Maintaining high database security standards can be costly. And sometimes, you don’t want to deal with the security risks involved.
That’s why Nexcess offers a fully-managed enterprise hosting service. A team of experts takes care of your database’s security and management so you can focus on other crucial aspects of your business.
Check out our enterprise hosting plans to get started today.