Cloud technology is one of the most powerful tools in today's fast-paced business world. It’s easy to see why — it delivers a wide range of benefits, such as improved decision-making, cost savings, and business continuity.
However, the risks associated with its use are cause for concern.
For example, according to a 2023 cloud security report by Cybersecurity Insiders, nearly all organizations are concerned about security in the cloud.
The good news? Enterprises that follow cloud security best practices can secure cloud assets and stay ahead of cyberattacks.
In this guide, we’ll walk you through what you need to know about enterprise website security and introduce you to a reliable cloud host that can help you achieve and maintain optimal enterprise security.
Keep reading to learn:
- What is enterprise cloud security?
- The importance of cloud security for enterprises
- Challenges in enterprise cloud security
- Best practices of enterprise cloud security
- Benefits of secure cloud hosting
- Benefits of Nexcess secure cloud hosting for enterprise security
- Final thoughts: Achieve optimal enterprise security with Nexcess secure cloud hosting
What is enterprise cloud security?
Enterprise cloud security involves the use of technologies, processes, policies, best practices, and procedures to secure an enterprise’s cloud assets against unauthorized use or malicious attacks.
Put another way, it involves protecting the cloud infrastructure, applications, and sensitive data from cyberattacks.
Security measures include data encryption, endpoint protection, threat hunting, authentication, and data classification.
Website security is so important to enterprises that 92 percent increased their cybersecurity budgets for 2023.
Now that you know what enterprise cloud security is, let’s look at the various reasons why it’s critical for businesses.
The importance of cloud security for enterprises
Cloud computing poses a unique set of security risks. In fact, 64 percent of participants in a Statista survey said their company trained its existing IT staff in response to changing security needs when moving to the cloud.
There are several reasons enterprises must secure their cloud environment — first and most importantly: data protection.
A data breach can have significant consequences, such as prolonged downtime, reputational damage, and decreased market value.
It can also shift a business’s attention from achieving core business goals.
Secondly, cloud security helps an enterprise maintain regulatory compliance requirements. Noncompliance can cause regulatory bodies to issue massive fines and penalties. For example, GDPR can issue fines as high as €20 million (about $21 million).
Staying compliant can also help you avoid significant legal problems. For example, when a breach occurs due to noncompliance, those affected (e.g., customers and vendors) may pursue legal action and file lawsuits in court, further damaging a business’s reputation.
Now let’s consider some of the top security issues or challenges affecting enterprises.
Challenges in enterprise cloud security
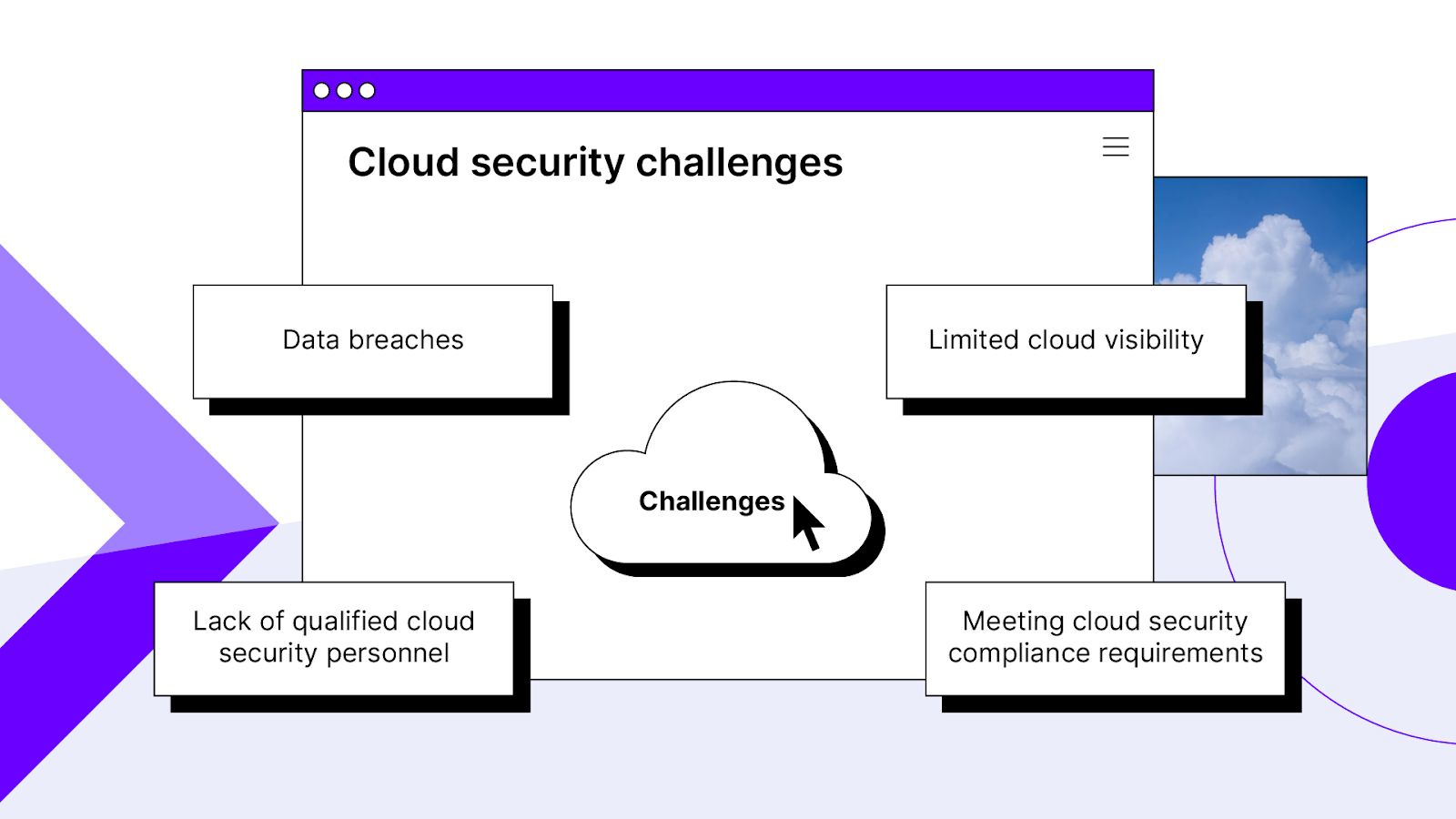
Enterprises shift applications and data over to the cloud to cut costs and tap into other benefits of cloud hosting. However, certain security challenges arise from making the shift.
Cloud environments require different security tools from on-premises systems, and there’s usually uncertainty about who is responsible for what.
Below are some of the most significant cloud hosting security challenges enterprises face.
Data breaches
Data is among a business’s most valuable assets as it informs decision-making, drives sales, and promotes scalability. So it’s unsurprising that data breaches remain a top concern among enterprises.
According to a 2023 Laminar report, data breaches in the public cloud increased from 51 percent in 2021 to 77 percent in 2022.
Breaches can occur due to unsecured APIs, misconfigurations, identity and access management (IAM) issues, and other cloud vulnerabilities.
Limited cloud visibility
It isn’t uncommon to find enterprises using a multi-cloud approach (i.e., two or more cloud providers), resulting in an expansive cloud footprint.
Valtix states that multi-cloud is one of 2023's top strategic priorities for 95 percent of organizations. However, such an approach can lead to limited cloud visibility, which can cause an enterprise to be unable to see an emerging threat and react accordingly.
Enhanced visibility helps enterprises detect security threats and mitigate risks such as data breaches.
Lack of qualified cloud security personnel
Certified cloud security professionals are crucial in maintaining and operating a secure cloud environment. According to a report by Cybersecurity Ventures, 3.5 million cybersecurity jobs will remain unfilled by 2025.
To that end, IT teams usually bear the brunt of the cybersecurity skills shortage. So if they lack the requisite knowledge, securing the cloud can become difficult and expose your business to cyberattacks.
Meeting cloud security compliance requirements
Ensuring continuous compliance in the cloud is something many businesses need help with. According to a 2022 IBM report, more than half of survey respondents say ensuring compliance is challenging.
This could be due to several reasons. For one, with continuously evolving compliance requirements, a business might fail to keep up with the latest changes.
Second, if customers are spread across the globe, a business may have a difficult time complying with the different kinds of laws that exist in these countries.
Best practices of enterprise cloud security
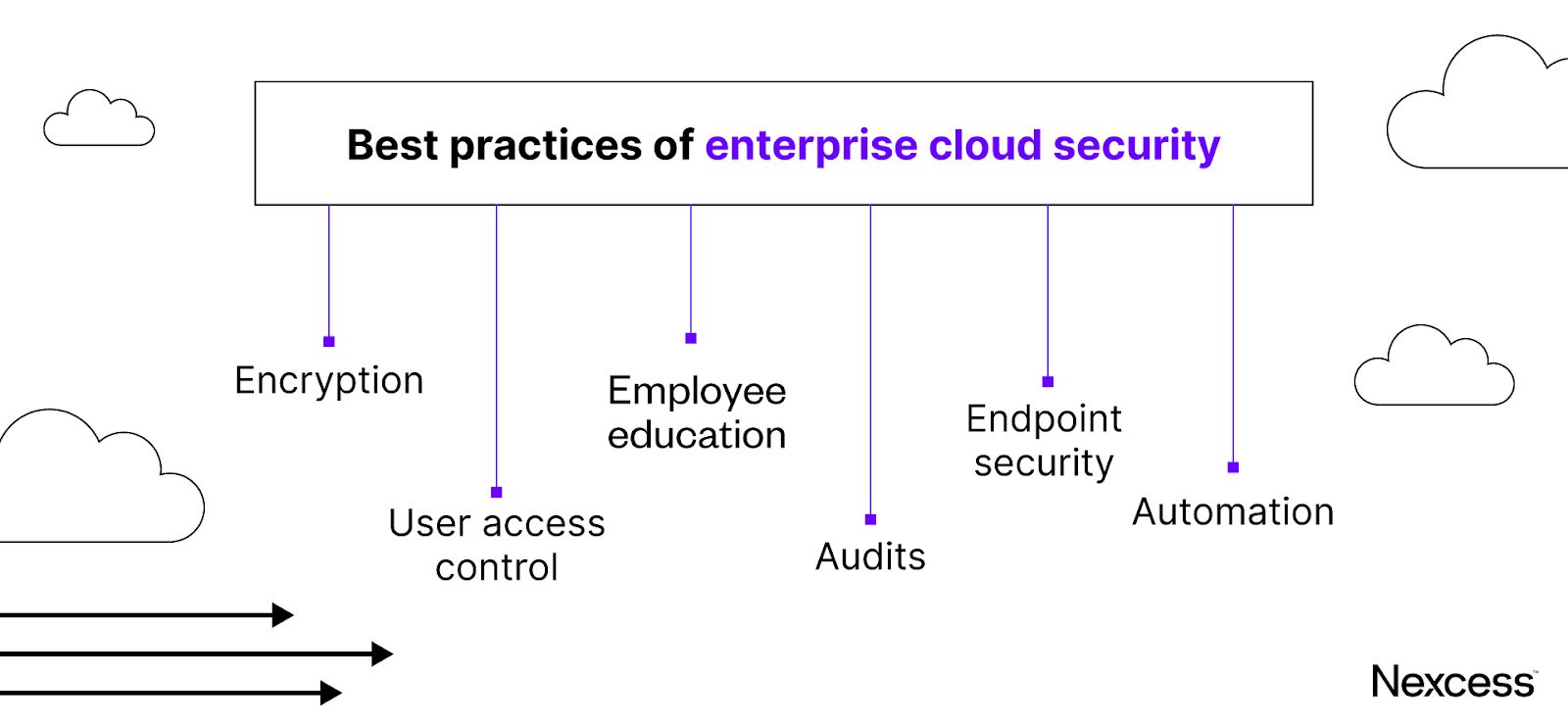
To maximize the benefits of transitioning over to the cloud, enterprises should implement various cloud security best practices:
- User access control: It’s crucial to implement tight controls around user access to enforce optimal data security. This restricts cloud data access to verified users (e.g., employees) and ensures that users have the right level of access based on their roles, among other factors. And when employees leave your company, you should revoke access to ensure data remains safe.
- Encryption: Cloud encryption uses algorithms to encode data before it’s stored in the cloud. Encrypted data is unreadable so unauthorized or malicious users can’t read it. For that reason, it’s one of the best ways to ensure cloud data can’t be compromised. And even if the data is stolen or lost, it’s useless without the encryption keys.
- Employee education: A 2023 Thales report cites human error as the primary cause of cloud data breaches. Uninformed staff can cause significant data breaches. To counter this, educate them about the various security threats (e.g., social engineering and phishing attacks) they can fall victim to.
- Audits: A cloud security audit can help you identify misconfigurations and determine whether existing security controls are functioning as expected. Furthermore, it can help you establish whether your business complies with industry standards.
- Endpoint security: Hackers can exploit user endpoints or end-user devices to gain entry into your cloud system. This requires investing in endpoint protection solutions such as anti-malware and firewalls.
- Automation: Automation protects your cloud workloads from security vulnerabilities. It also provides added benefits such as enhanced security posture and minimal manual errors.
Benefits of secure cloud hosting
The benefits of secure cloud solutions are numerous and include the following:
- Loss prevention: Data stored on the cloud is easily accessible with an internet connection and from any device. You won’t lose access to crucial data should something happen to your local hardware.
- Reliability and uptime: If a physical server malfunctions, you’ll still be able to serve content to users since cloud hosting includes a cluster of servers spread across the network. As a result, your website maintains uptime.
- Scalability: Cloud infrastructure scales resources up or down to suit your needs without the possibility of downtime. For instance, you get scalable cloud storage and pay for it based on usage rate.
- Analytics: On-premises analytics may limit your ability to make full use of stored data. In contrast, cloud-based analytics let you easily track and analyze complex or large data sets, resulting in increased revenue. Alteryx backs this up by stating that cloud analytics has increased profitability for 89 percent of organizations.
To harness the full potential of enterprise cloud hosting and minimize security risks, you’ll need to partner with a reliable cloud hosting provider like Nexcess.
Benefits of Nexcess secure cloud hosting for enterprise security
Nexcess is a leading hosting provider that was founded over 20 years ago. It was built with a focus on speed and scalability, and boasts features such as a built-in CDN and autoscaling.
In addition to WordPress, Magento, and WooCommerce hosting, Nexcess offers several cloud hosting plans with cost-effective pricing. What’s even better is that it includes enterprise cloud security.
Plus, Nexcess handles the technical aspects of security and compliance. That’s in contrast to a public cloud service provider — such as Microsoft Azure and Amazon Web Services (AWS) — where it’s mainly up to the end user.
Below are key security features that come with Nexcess cloud hosting services:
- Daily backups (archived for 30 days).
- SSL certificates.
- Web application firewall (WAF) with regular updates.
- GDPR, PCI DSS, and SSAE-18 compliance.
- Uninterrupted server monitoring.
- Advanced user management.
Plus, you’ll get backend maintenance to ensure everything stays in tip-top shape. You can even host different content management systems (CMSs) in a single hosting plan.
Final thoughts: Achieve optimal enterprise security with Nexcess secure cloud hosting
Protecting your enterprise from security threats is no small task. That’s why you must take proactive steps to identify and mitigate these threats.
This requires choosing a trustworthy cloud platform with up-to-date security measures and robust features.
At Nexcess, our cloud hosting plans are equipped with the latest technology, support for PHP-based applications, DevOps support, and more. You can rest assured your business is in safe hands.
Explore Nexcess secure cloud hosting today.

