Many owners of small and medium sized businesses make the mistake of believing that because their website is small, cyber criminals won’t bother attacking them. This couldn’t be farther from the truth.
In 2021 alone, small and medium-sized business websites experienced 228 million security threats a month — double the number recorded in 2020.
Such a dramatic increase in volume begs the question, how are cybercriminals attacking websites so efficiently?
The answer is robots — or just bots.
Bots, not humans, will be the most frequent visitors to your new website. In fact, that’s an understatement: The annual security report put out by SiteLock estimates that websites receive 5.5 times more traffic from bots than from humans — about 2,306 visits a week on average.
And to make matters worse, SiteLock reports that 60% of those bots come to harm your website. That’s approximately 1,384 malicious bot visits a week, or a little over 70 thousand a year.
Clearly, you need to do everything possible to protect your website from cyberattacks. And the first step is to choose a secure hosting provider.
In this article, we’ll explain what secure web hosting is, why it’s important, and what factors you should consider when choosing a secure web host.
- What is secure web hosting?
- Why is secure web hosting important?
- Secure web hosting: What should you look for?
- How to identify and protect against security vulnerabilities
- Final thoughts: Secure web hosting
What is secure web hosting?
Secure web hosting describes web hosting services that focus on protecting your website and its visitors from cybersecurity incidents. Secure web hosts make that possible by offering security features like:
- Firewalls.
- Network monitoring.
- Malware detection.
- Regular backups.
- DDoS protection.
When searching for a web host, it’s important to look for ones whose plans come with a variety of these features already in place. Otherwise, you may be responsible for paying for these security necessities out of pocket to protect your website and its visitors.
Get secure web hosting from Nexcess
We pride ourselves on complying with industry standards to provide the best web hosting security
Why is secure web hosting important?
Your web host’s in-built security features are the first line of defense against malicious bot attacks.
And far from diminishing, these bot attacks are becoming more common and dangerous. SiteLock estimates that in 2021 the rate of infection of websites with high-severity malware — which targets the data of visitors — was 26%. That’s double what the rate was in 2020.
It’s no surprise then that people are becoming more cautious about what kinds of sites they visit.
According to data collected by the Baymard Institute, 18% of people opted not to purchase on a website because they didn’t trust it with their credit card information.
The easiest way to combat this is to make your website as secure as possible, on the front end and the back. And that means hosting your website with a web host that prioritizes security.
Potential customers won’t be the only ones scrutinizing your website’s security either. Many states and countries now have laws to protect how people’s digital information is used and stored.
Fail to comply, and you and your business could face legal ramifications.
Secure web hosting: What should you look for?
Here are the essential factors you should consider when determining if a web host is secure:
- Secure information transfer.
- Firewalls.
- Physical server security.
- Network and resource monitoring.
- Domain name security.
- Type of hosting service.
- Malware detection and removal.
- Backups.
- DDoS protection.
- Customer support.
Secure information transfer
Secure hosting providers typically use the Secure Sockets Layer (SSL) or Transport Layer Security (TLS) protocols to encrypt network traffic, to make it unreadable (and therefore unexploitable) by malicious actors.
A secure web host should include SSL certificates with its hosting packages for free. In this way, any website you create will use HTTPS in its web address to let the users know their information will be protected.
The web host should also support Secure Shell (SSH) and SSH File Transfer Protocol (SFTP) to encrypt remote communication with its servers.
Firewalls
A web application firewall (WAF) helps block unwanted visitors from accessing your website by monitoring and filtering the incoming internet traffic.
In addition to blocking traffic from blacklisted IP addresses, a WAF can also monitor and detect malicious content, as well as analyze network traffic to detect current and emerging cyberattack patterns that hackers use to compromise systems and cause downtime.

If the worst happens and your website is compromised, a firewall can also detect and prevent harmful content from leaving your site and spreading further.
Web hosting providers include WAFs as part of their infrastructure, but knowing more about how they are configured can help determine how secure the host is. At Nexcess, we use the web application firewall ModSecurity to protect your websites from intrusion.
Physical server security
A hosting company’s physical security is just as important as its network and software security. When talking about a web host’s physical security, we mean its offices, servers, and other infrastructure critical for keeping its websites up and running.
A secure web host will have the necessary measures in place at its facilities to prevent unauthorized access. These measures include:
- Security doors.
- Access control systems.
- Cameras.
Basically, the web host should monitor all physical server interactions and operations to prevent tampering.
In addition to these security measures, a secure web host should also have disaster recovery and business continuity plans if everything else fails.
Before deciding on a hosting provider, investigate how it handles physical security. Some quick research on its website should reveal what you need to know.
For instance, Nexcess discloses that it chose all its data centers with security in mind. Each Nexcess data center is protected by advanced security tools, additional redundancies, and a 24/7 support team.
Network and resource monitoring
Monitoring systems are designed to inform you of security incidents and help you understand the potential impact.
Depending on the hosting plan you select, the monitoring systems available to you may vary from simple alerts to notifications of outages to more complex dashboards that show real-time resource usage, server uptime, and network traffic.
Make sure the hosting provider you opt for lets you customize notifications. For example, you may want one type of alert for when bandwidth use is high and another for detecting an intrusion attempt.
Domain name security
Some web hosts provide domain name management as part of their services, letting you purchase, transfer, and manage domain names for your websites.
But domain name management comes with a host of security risks including:
- Register hacking.
- Cache poisoning.
- Domain name system (DNS) spoofing.
- Denial-of-service (DDoS) attacks.
Common security features that protect against these attacks are a registrar lock to stop your domain from being transferred without your permission, renewal notifications to alert you before your domain expires, and privacy services to hide the contact information associated with your domain.
Make sure the hosting provider you opt for includes these security functionalities.

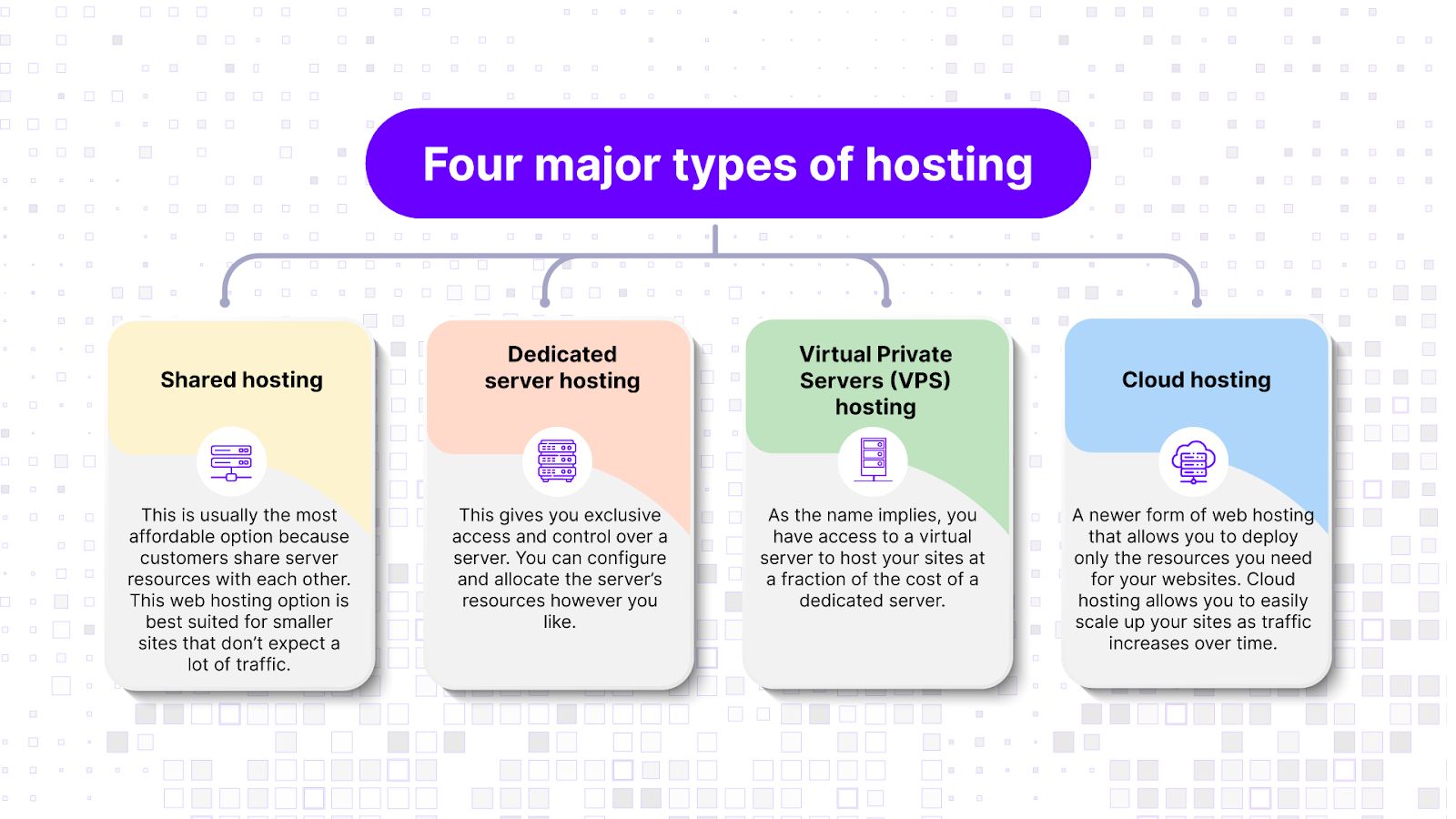
Type of hosting service
Every web hosting plan has its inherent strengths and weaknesses.
For instance, a shared hosting plan is often inexpensive and appears as a straightforward choice for a budget-conscious customer. However, a shared hosting plan means there’s a single web server housing multiple websites — which means there’s a risk of malware spreading from the neighboring websites.
On the other hand, managed hosting plans, which typically include monitoring services and a more hands-on approach to security from the service provider, are generally more secure.
Malware detection and removal
Malicious software, also known as malware, is a common attack tool for hackers, with over 5.4 billion malware attacks detected in 2022.
To safeguard customer websites against this kind of attack, web hosts include malware scanners as part of their security arsenal. These tools automatically scan your website's various files and folders to detect harmful content.
When they detect malware, depending on their configuration, a scanner will either totally remove the malware or quarantine it and alert you of its existence. However, auto-quarantine is not yet enabled on all cloud hosts. If malware is detected, you’ll be notified but it would be up to you to take the next steps on cleaning up and securing your site.
Backups
If you ever experience a data loss or your website is compromised and becomes unrecoverable, backups are what will help you get back up and running. The best web hosts offer automated daily backups to ensure that your last recovery point isn’t too long ago.
Another backup feature you should pay attention to is the retention time. In other words, how long does the web host company keep website backups before deleting them? The longer the retention time, the better for you.
DDoS protection
Distributed denial-of-service (DDoS) is another common attack vector for hackers. These occur when a hacker uses multiple sources to flood a victim’s network or website with so much traffic that it becomes unavailable to regular users.
Most hosts use content delivery networks (CDNs) like Cloudflare to protect against DDoS attacks.
Customer support
Things will inevitably go wrong with your website. It’s just the way it is. And while you can probably troubleshoot most issues on your own, it’s nice to know that your web host has your back if the need arises.
Most web hosts offer some tech support, but not all of them make it easy or convenient to receive assistance.
What sets web hosts with good customer support apart from those without it is the responsiveness of the team and the quality of the support.
Responsiveness means you can request support any time of the day, and you’re guaranteed to receive a response. For instance, Nexcess offers 24/7 phone support because it’s just faster to resolve issues through speech than text.
Likewise, the quality of the support you receive is just as important as its availability. You want to know the person assisting you is an expert in their field who can quickly diagnose and resolve any problem you might have.

Checking customer reviews (from multiple sources) is a good way to gauge the level of customer support a web host might offer.
Don’t worry if there are a couple of bad reviews — these are bound to happen. But if every review has something negative about customer service, it’s best to find another web host.
How to identify and protect against security vulnerabilities
While a secure host bears the bulk of the burden in ensuring the security of its hosting services, as a website owner, you also have a role to play in maintaining your website’s security.
According to a 2022 Verizon report, 82% of data breaches involved some level of human error.
Here are some security measures you can use to protect your website against cybersecurity threats:
- Make the most of the account security provided by your hosting service. Use a secure password for your web hosting account, website control panel, databases, and all other parts of your website hosting plan that require secure access.
- Enable two-factor authentication where applicable for increased security. Use an authenticator app like Google Authenticator instead of a text message or email account for your second authentication method.
- Update your website regularly. This might take the form of plugin updates for your website’s content management system, PHP version updates, antivirus updates, or security fixes for other parts of your website. But make sure to test the updates on a development environment before pushing them to your live website.
- Do your own manual backups. Even when your host has automatic backup plans, you can never have too many backups.
- Install security plugins. If you use a content management system like WordPress, you can install several security plugins to improve your website's security. Note: all managed WordPress and WooCommerce plans from Nexcess come with Solid Security Pro free of charge.
Final thoughts: Secure web hosting
Cybersecurity threats are a constant issue in our increasingly connected world.
As malicious agents develop more advanced techniques to attack systems and compromise data, it’s more critical than ever that you do everything possible to keep your website’s, your site’s visitors’, and your data secure.
To avoid becoming a victim, you should select a hosting partner that will help you beat the odds with contemporary security solutions for your website. At Nexcess, we pride ourselves on complying with industry standards to provide the best web hosting security.
Try our managed hosting solutions for the best in secure web hosting.