DNS poisoning is a threat to both individuals and organizations alike. Keep reading to learn about DNS poisoning attacks and how you can protect yourself.
What is DNS Poisoning?
DNS poisoning is a spoofing activity in which hackers redirect original traffic to a fraudulent website. DNS poisoning makes it easy to access sensitive information on a device or in the interrupted web traffic flow.
How Does a DNS Poisoning Attack Work?
DNS stands for Domain Name Server (DNS). In DNS cache spoofing, hackers use altered DNS records to redirect web traffic. When legitimate users enter a web address, they land on a different website than they intended.
The worst thing is that the user has no idea because the fake websites look like original sites. From there, hackers can easily perform malicious activities on your device after a DNS attack.
In a DNS poisoned device, hackers can install a virus to damage data and information, steal login credentials from the device, track bank transactions, or even install a worm that can damage other devices.
How Risky is a DNS Poisoning Attack for Organizations?

DNS poisoning is a spoofing cyber attack that puts both users and organizations at risk. Once your device has fallen victim to a DNS poisoning attack, it becomes challenging to resolve. Most users don't have any idea of the malicious activity.
In DNS cache poisoning, hackers alter the original DNS cache with false information or addresses. It can be tough to track and solve this problem because the affected device will return to a false website by default.
Related reading: Top 3 Website Security Threats To Prepare for in 2022 >>
Most hackers try to build a fake website that looks identical to a genuine website. In such cases, users don’t realize the website was fake. Sometimes, users can enter their sensitive personal or business information without knowing it is a fake website.
Other risks associated with this type of cyber attack include:
Viruses and Malware
Hackers can easily install malware software or viruses on a device once users are directed to a fraudulent web address. After successfully installing a virus on the device, they can access all data in the device and use it for malicious activities. They can also install viruses in a user's device to damage device data or other devices that connect with it.
Theft
DNS poisoned devices are at high risk of information and data theft. Hackers can easily get away with stealing important personal as well as business information from the device. They can access sensitive information like social security numbers, house property data, or even payment details and logins.
Related reading: Ecommerce Site Security: 10 Step Audit for Ecommerce Stores >>
Security Blockers
Security blockage is another significant risk factor of DNS poisoning attacks. Spammers can redirect traffic from security providers to fake websites. It blocks devices to get critical security updates and essential information for strong device security. This approach causes severe long-term security damage that exposes devices to other security attacks like Trojans or viruses.
Censorship
Recently, a few cases of government censorship from some countries have been reported. The governments used DNS poisoning to censor certain information from websites. It allowed the governments to block specific information or traffic from websites that they didn't want shown to citizens.
How DNS Works
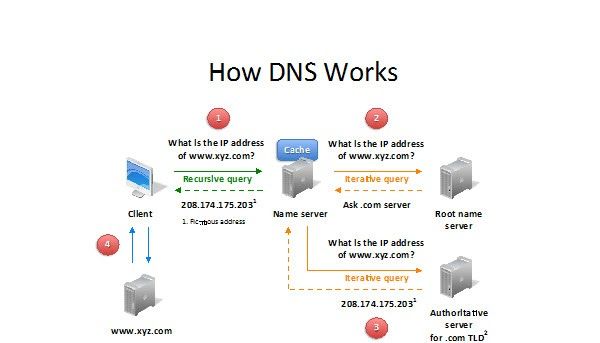
It is essential to understand the working techniques of DNS in order to understand DNS poisoning methods. Paul Mockapetris designed the DNS system in 1983 — an era when there were only a few servers and websites on the internet.
The DNS system was created with a few special security measures. DNS developers never imagine someone could manipulate a DNS system to defraud users.
Web programmers prefer to use short, user-friendly web addresses in their websites. It helps websites perform better in query results and also helps users to know what a page contains before clicking on it.
However, computers only understand information in a specific language. They don't understand the web address that humans use. When you type a web address in your browser’s search box:
- Your device contacts a DNS server to get more information about the entered web address.
- The computer understands the web address made up of dots and numbers only. The DNS looks up numerical addresses in its server.
- If your device has never visited this web address before, it contacts another server to get access to other information.
- The DNS server completes the query about the entered web address by switching it to a numerical version.
- The user is directed to the required web address. The DNS server sends you to the proper website server that hosts your web address.
- The data is stored in the form of a cache. The DNS server stores web addresses from the human version to the numerical version for future use.
Methods for DNS Spoofing or Cache Poisoning Attacks
Hackers use various methods for DNS cache spoofing or poisoning. Some standard DNS poisoning methods include:
DNS Server Hijack
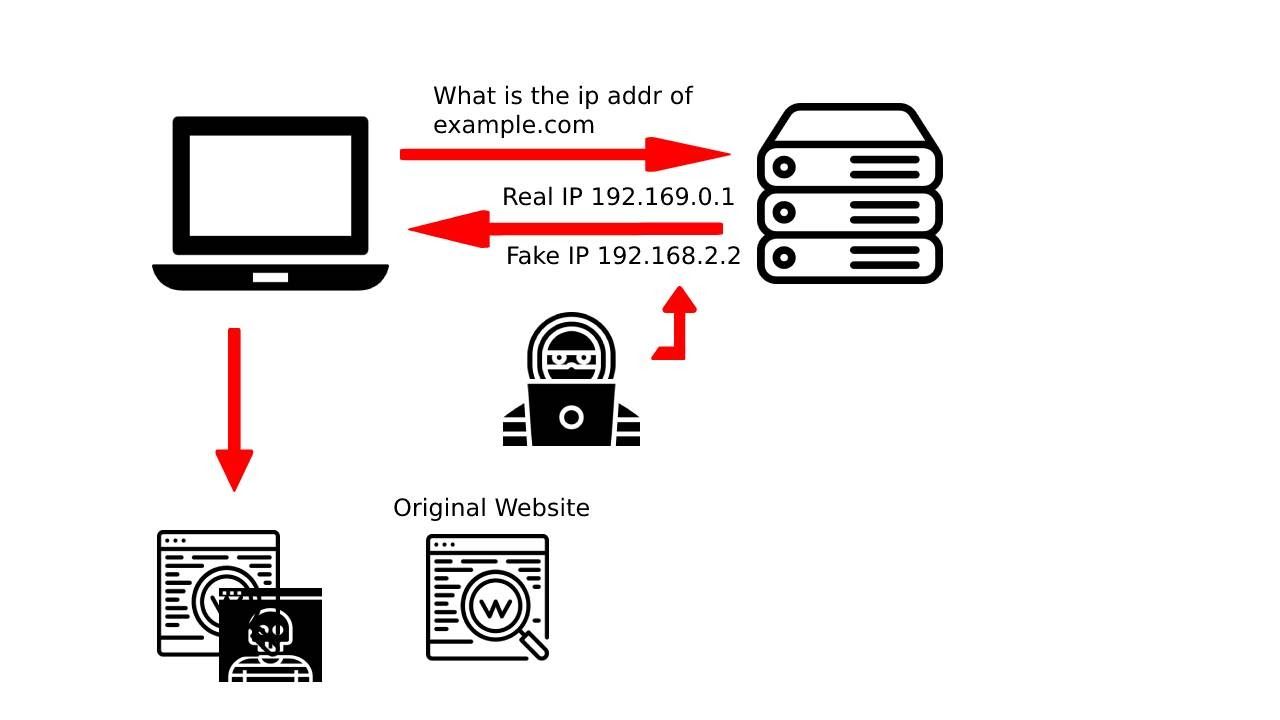
Spammers reconfigure the DNS server to direct all requesting visitors to a fraudulent website. Once a spammer hijacks the DNS server with a fake DNS, all IP address requests from the poisoned domain land on the fake malicious websites.
Man-in-the-Middle Duping
In this method of DNS spoofing, the hacker steps between your DNS server and web browser to spoof both. Hackers use spoofing tools or software simultaneously on your local device to poison cache and DNS poisoning to infect DNS servers.
DNS Cache Spoofing Via Spam
Hackers often send poisoned DNS cache URLs to users through spam emails. These emails are designed to convince the user to click on the provided URL, which in turn poisons their device. Images or files from spam emails or untrusted sites can also redirect users to fake websites. Once you are directed to these websites, your device is spoofed with a malicious virus.
How to Prevent DNS Poisoning
You might be wondering how you can protect your device from DNS poisoning. From a user perspective, there are limited ways to prevent DNS spoofing.
Related reading: 10 Web Hosting Best Practices for Ecommerce Security >>
However, website owners and server providers are more authorized to secure themselves and their users. Both server providers and users can practice safe browsing with the following tactics.
Endpoint users can avoid DNS poisoning by:
- Never click on an unauthorized link or URL.
- Regularly scan your device for malware or virus.
- Use VPN (Virtual Private Network) for browsing.
- Remove DNS cache to avoid cache poisoning.
Website owners and DNS server providers can avoid DNS poisoning by:
- Use of a DNS poisoning detection tool.
- End-to-end data encryption.
- Use of domain name system security extensions.
Prevention Tips for Endpoint Users
As an endpoint user, there are a few ways that you can use to avoid DNS poisoning. You can practice these simple steps.
1. Never Click an Unauthorized Link or URL
You can receive many links through social media platforms, text messages, or spam emails. Avoid clicking on any unrecognized link as much as possible. Always enter the original web address in your search browser manually to be on the safe side.
2. Regularly Scan Your Device
It can be challenging for users to track and detect malicious viruses or malware in their device. Security software can help you to find and remove any hidden malware.
Poisoned websites can inject all types of malware into your device. So, regularly scan your device for all types of viruses, spyware, and other hidden spoofs.
3. Use a VPN for Browsing
A VPN (Virtual Private Network) provides you with safely-encrypted browsing. Private virtual networks use end-to-end encryption for traffic. Use one of the best VPN service providers, which will give you access to end-to-end encrypted DNS servers. This will help you to avoid redirecting towards fraudulent websites.
4. Remove DNS Cache to Avoid Cache Poisoning
Poisoned DNS cache stays in your device for a long time, unless you remove all DNS cache from your device. Use the DNS cache removing method according to your device to remove it from infected web address.
DNS Poisoning Prevention Tips for Website Owners

The safety of users from DNS spoofing attacks is the responsibility of website owners and DNS service providers. Website owners can practice several steps to avoid DNS poisoning. As a website owner, you can follow any of these DNS safety measurements.
1. Use DNS Poisoning Detection Tools
DNS detection tools actively scan all data before receiving and sending it out to users. It helps to detect any malware and virus in the data.
2. End-to-End Data Encryption
Sending and receiving encrypted data keeps it safe from hackers. Spammers cannot duplicate the unique security codes for the original websites.
3. Domain Name Security System Extension
This is a “DNS verified” domain security label. It helps a DNS to look up authenticity and prevent it from DNS poisoning.
Bottom Line
DNS poisoning attacks are prevalent and very dangerous. And unfortunately, it’s complicated for users to track any such activity on their devices — especially if you are affected by DNS cache poisoning. Since these problems are hard to solve, it’s best to prevent them in the first place.
Follow these safety steps to protect your device from DNS poisoning attacks.
And choose a host who provides added security to your website — like Nexcess. Fully managed hosting plans come with security features such as daily backups, automatic updates, and free tools.
Check it out to get started today.
